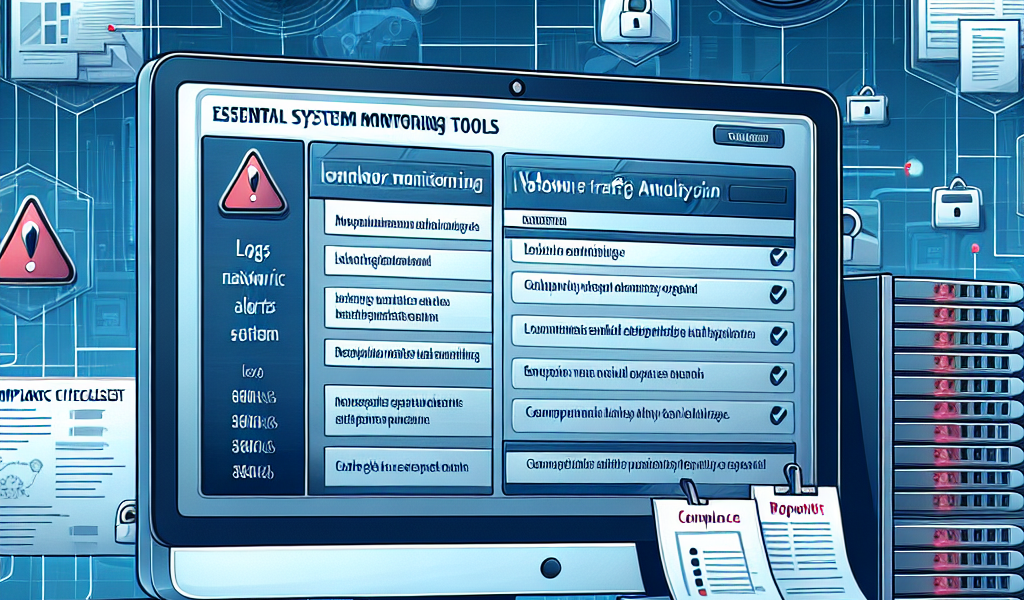
In the realm of law enforcement and criminal justice, ensuring the integrity and security of sensitive data is paramount. The challenge is not only to comply with the Criminal Justice Information Services (CJIS) security policy but also to maintain a robust and proactive approach to system monitoring. CJIS Ready system monitoring tools are crucial for organizations striving to fortify their security posture while ensuring compliance. Unfortunately, many agencies struggle to find comprehensive solutions that address their unique needs, exposing them to risks of data breaches and legal repercussions. This article dives deep into essential system monitoring tools that can elevate compliance and security monitoring standards in line with CJIS requirements, equipping your agency with the knowledge to protect crucial information effectively.
Key Features of CJIS Ready System Monitoring Tools
When selecting CJIS Ready system monitoring tools, it’s essential to identify key features that ensure comprehensive compliance and security. First and foremost, real-time monitoring capabilities are non-negotiable. These tools must provide continuous oversight of network activities, enabling agencies to detect unauthorized access attempts or unusual behaviors as they occur. This proactive monitoring approach not only aids in compliance but also fortifies the overall security framework against potential threats.
Another critical feature is robust reporting capabilities. CJIS compliance demands that agencies maintain meticulous logs of all activities related to the access and use of criminal justice information. Effective monitoring tools should generate automated reports that capture relevant data, ensuring that agencies can demonstrate compliance during audits or investigations. Such reporting capabilities also allow for trend analysis, providing insights into potential vulnerabilities or areas requiring further attention.
Lastly, integration with existing security infrastructure cannot be overlooked. CJIS Ready system monitoring tools must seamlessly connect with other security solutions—such as identity management systems, firewalls, and intrusion detection systems—to provide a holistic view of an organization’s security posture. This interconnectedness enables agencies to create a layered defense strategy that not only meets compliance but also empowers them to respond swiftly to emerging threats.
Top Recommended Tools for Compliance and Security Monitoring
When it comes to CJIS Ready system monitoring tools, several options stand out for their effectiveness and reliability. One of the top contenders is Splunk, a powerful platform that provides real-time visibility across the entire IT landscape. Splunk’s ability to ingest vast amounts of machine data, combined with its advanced analytics capabilities, makes it invaluable for compliance monitoring. Its customizable dashboards and automated reporting features specifically cater to CJIS requirements, allowing organizations to track compliance effortlessly.
Another notable tool is LogRhythm, recognized for its exceptional Security Information and Event Management (SIEM) capabilities. LogRhythm’s platform utilizes machine learning to detect anomalies and potential threats, thereby enhancing proactive security monitoring. Its compliance dashboard allows organizations to visualize their adherence to CJIS standards, making it an essential tool for agencies focused on maintaining compliance while ensuring the security of sensitive data.
Lastly, SolarWinds offers an array of system monitoring tools that can be tailored to meet CJIS compliance needs. With features like network performance monitoring and log management, SolarWinds provides agencies with the tools necessary to oversee data access and identify potential vulnerabilities. The ease of use and powerful reporting functionalities position SolarWinds as a strong option for organizations looking to enhance their CJIS compliance strategy.
In a landscape where data integrity and security are non-negotiable, investing in CJIS Ready system monitoring tools is essential for law enforcement agencies and organizations handling sensitive information. By understanding the critical features required for compliance and exploring top recommended tools, agencies can significantly enhance their monitoring capabilities. It’s time to take your compliance efforts to the next level. Equip your organization with the knowledge and tools necessary to safeguard sensitive information and navigate the complexities of CJIS compliance with confidence. Don’t wait—act now and ensure your agency is protected against the ever-evolving landscape of cyber threats and regulatory requirements.